Nearly all companies infrastructure have been compromised.
Most companies don't have enough man power to defend most intrusions!
We are here to help to defend your data.
Why use Split Encryption™ products?
To protect your data, we encrypt it with multiple encryption keys and then split the data and the encryption keys into multiple sections. We then distribute those individual sections to your server(s) and our server(s). Only a defined percent of your encrypted data and keys will be distributed to your server and the remaining data is stored on our data servers. We use a random encryption key for every individual record. This data is NEVER stored 100% in a single location. You sensitive data cannot be reconstructed without reconstructing all of the data and keys from the multiple servers. By default, only whitelisted IP addresses are able to decrypt the data. Only your server can decrypt your data, it cannot be decrypted from any other IP address. Our Split Encryption™ products reach beyond HIPAA, PCI and GDPR compliance.
Decentralized Data Center
Your data will be stored on multiple servers. Your data is unusable to intruders. Your data center(s) and our data centers will never store 100% of your encrypted data or encryption keys, only the partial data will be stored at each data center.
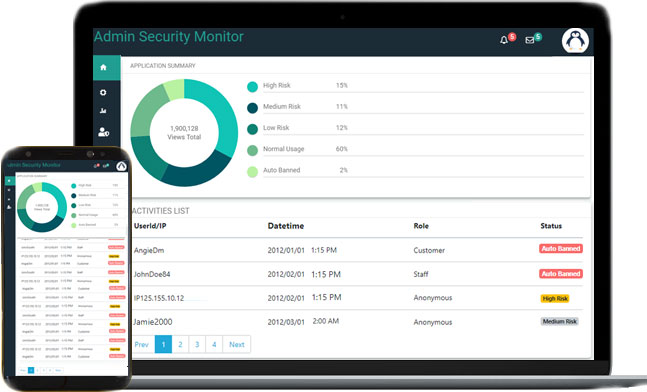
Auto Block Access
The system will block users from accessing data once they reached the threshold that is defined by you. You can control your employees and the public individually.
Instant Notifications
Send push notification to mobile applications, admin portal, and email before we lock down your user from accessing your sensitive data.
Can you guarantee your data is safe from cyber attack and can't be decrypted from cyberthreat? We can! As of now, nobody can decrypt our clients data or our data, even we can't decrypt the data on servers. Why and How? To decrypt the data, you would need to have all of encrypted data from multiple servers and all the encryption keys and to be on the whitelist to decrypt the minimum of 256-bit Advanced Encryption Standard (AES). We restrict access based on individual usage by IP and/or user account.
Business Collaboration
|
1
|
SIGN UPIt only takes a few minutes to enroll, our automatic activation will save you time and money. |
|
2
|
INTEGRATIONWe have technical training documentation and videos to show you how to integrate your data with our system. We have code samples for most machine languages C#,VB.NET, F#, PHP, Python, Node.Js, Java(JSP), Ruby, Perl, CFM. Click here to explore the developer area. |
|
3
|
WE DETECT, ALERT AND LOCKDOWN INTRUDERSThe system will automatically alert key users by email, mobile application, and the admin web application to automatically lockdown intruders. |